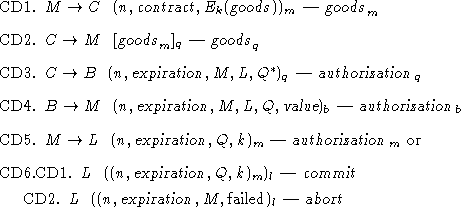
Figure 4: Full Certified Delivery purchase protocol.
The last and most intricate variation on the protocols is the addition
of support for two-way certified delivery, which is detailed in Figure
4. Our protocols provide
one-sided certified delivery; only the consumer can prove what goods were delivered.
If the burden of proof is expected to fall on the merchant, then the
purchase protocol can be changed to provide full certified delivery at
the cost of extra complexity. First, we introduce the notation
![]() to indicate the signature of M with key x without the
plaintext, e.g.,
to indicate the signature of M with key x without the
plaintext, e.g., ![]() for RSA signatures. If we provide
the merchant with Q and
for RSA signatures. If we provide
the merchant with Q and ![]() , then the merchant will be
able to prove what goods were delivered to the holder of Q. The
merchant must additionally be able to prove that the holder of Q is
the consumer for whom the transaction was processed. Our purchase
protocol for certified delivery follows:
, then the merchant will be
able to prove what goods were delivered to the holder of Q. The
merchant must additionally be able to prove that the holder of Q is
the consumer for whom the transaction was processed. Our purchase
protocol for certified delivery follows:
The new step, 2, supplies the merchant with the signature by q of the goods description. The inclusion of Q in 3 enables the merchant to link Q with the payment to be received. The logging of Q in CD1 associates Q with the completed transaction. To increase the trustworthiness of this association in case of corruption by one or more parties, the cryptographic time-stamping variation described above should be employed. In variants where Q may be reused, the log entries should be encrypted to prevent unassociated parties from linking the repeated uses of Q.